When using Application Control for Business which is the ultimate dream from a security perspective to only allow signed and trusted executables to be executed on our Windows devices. That requires that all binaries are signed, both executables and dll files (which are executables).
WIX Toolset is widely used to create Windows Installer packages even by Microsoft. The challenge is that the Custom Action .dll included in the WIX toolset is not signed, which causes a lot of challenges. This affects Intune agents as well, for example Device Inventory Agent, Intune Management extension and EPM agent. Even if we trust Microsoft signed code and use Trusted Installer the WIX dll’s are not signed.
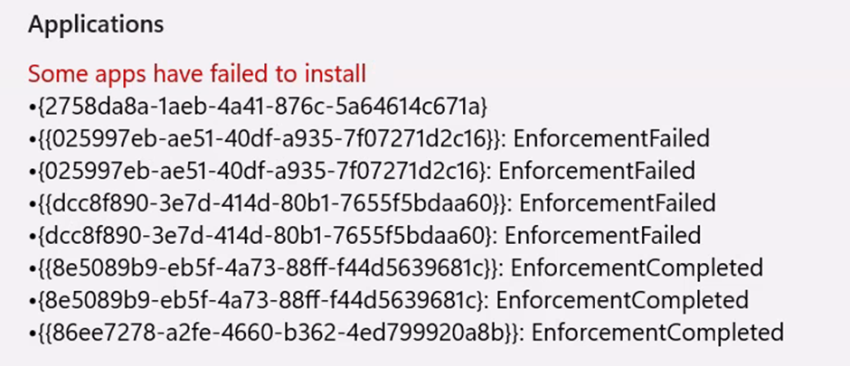
The first place we identified the error was in settings, Access work or School and Information under the “Managed by” section.
It will look like this in the different event logs.
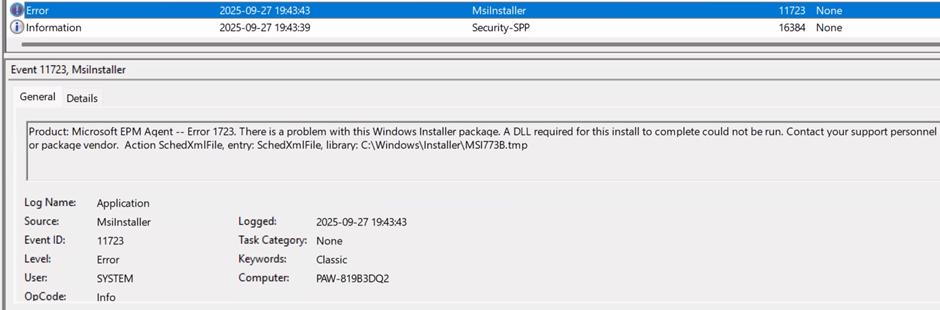
Application event log – we find the name of the Product that fails to install.
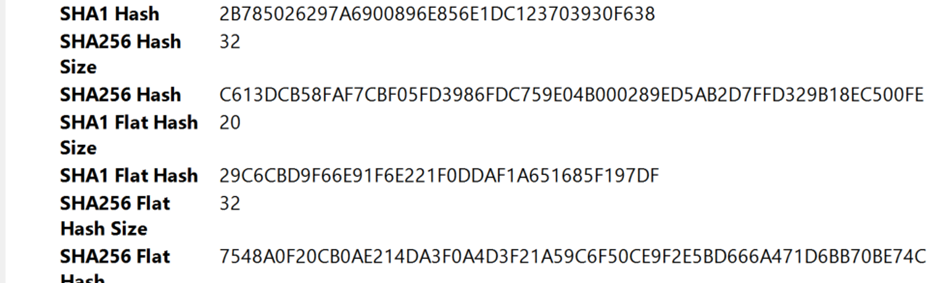
Codeintegrity event log – we find which file it is and the hash
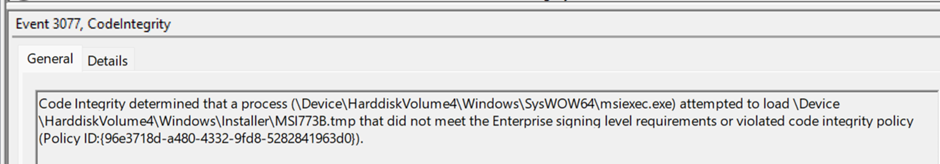
Looking at the details of the event entry, we see that it is a WiX custom action dll
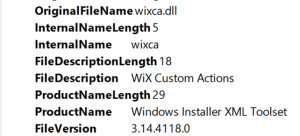
This means we need to create a hash-based rule to allow those Custom Action WiX dll’s to run during installation. The good thing is that all the information needed is in the event log entry. Which means we can open the saved evtx file on a different computer.
Let’s look at how we can detect this and create a supplemental Application Control for Business xml file.
Note: Device Inventory Agent and the EPM agent are installed by the MDM agent and not our trusted installer – Intune Management Extension
Create a supplemental rule
We have all the information we need in the Codeintegrity event entry as shown above, it is easier to use a tool like Microsoft App Control Wizard or the AppControl Manager tool which is available in the Microsoft Store. https://apps.microsoft.com/detail/9PNG1JDDTGP8?hl=en-us&gl=SE&ocid=pdpshare
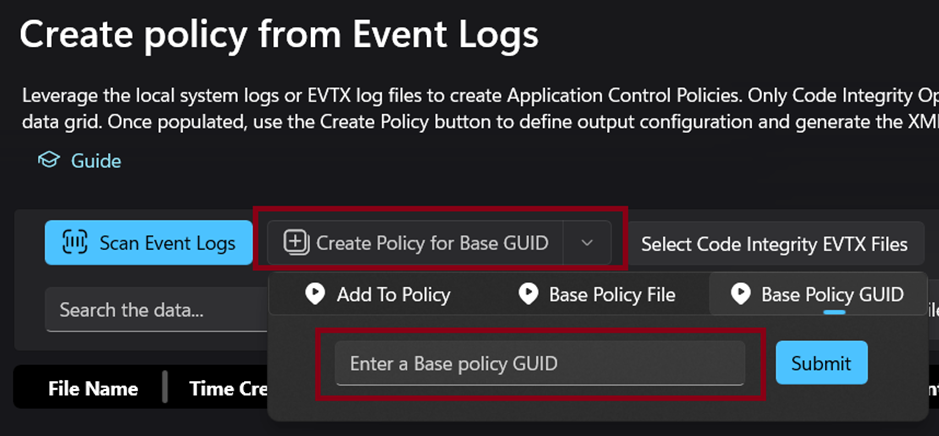
We need the basepolicy GUID to be able to create a supplemental policy as a supplemental policy must reference an applied basepolicy otherwise our supplemental policy is not valid.
- Launch AppControl Manager Tool
- Select the option to “Create policy from Event Logs”
- Select “Create Policy for Base GUID”, and enter your Base policy GUID
- Then select “Code Integrity EVTX files”, as I have it saved on my own computer.
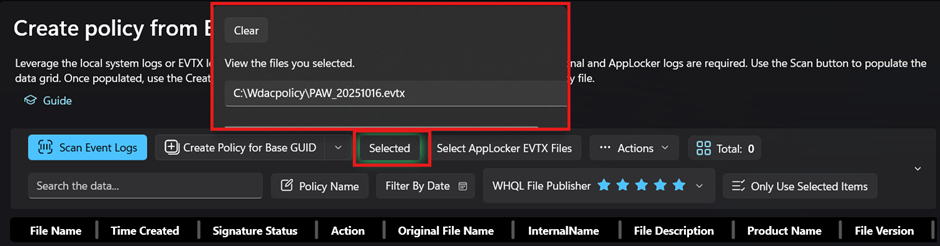
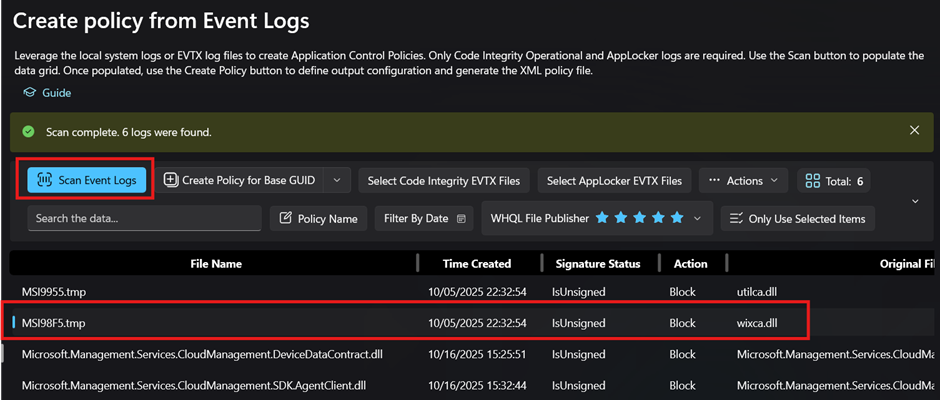
- Click “Scan Event Logs” and locate our blocked wixca.dll and we can also see that there is no signature as it is not signed
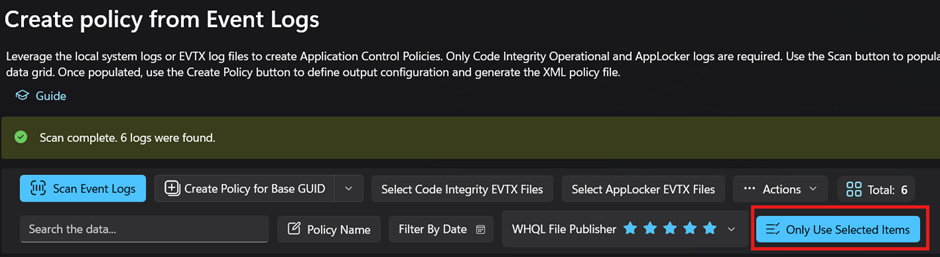
- Select “Only Use Selected Items”
- Then “Create policy from Event Logs” and our policy is created, we can test ut out our local machine under “Additonal Actions” but in my case I want to edit it first.
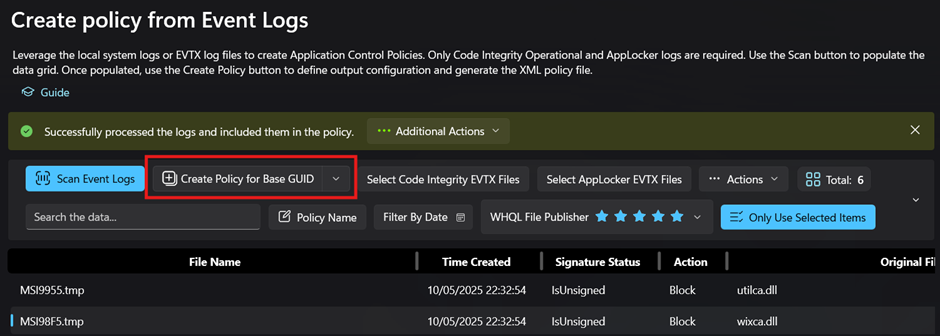
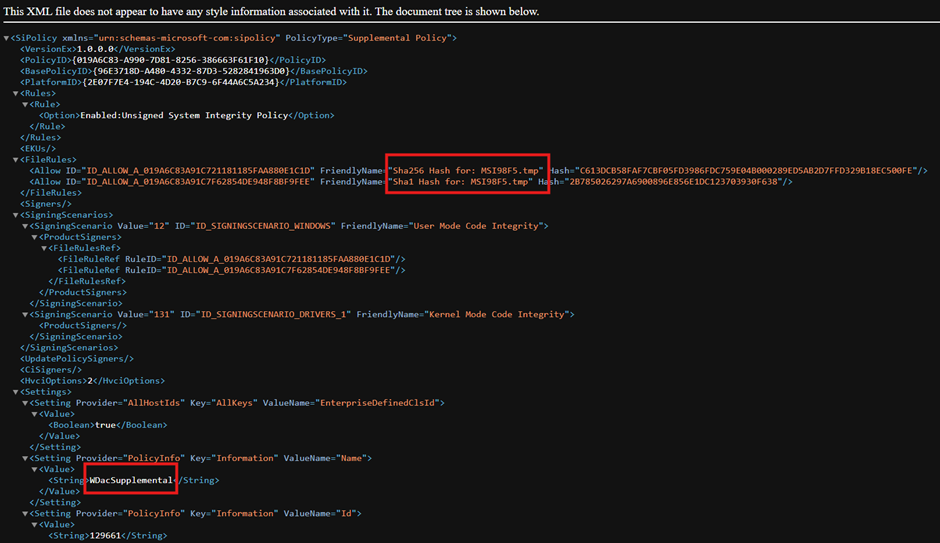
- I recommend editing the newly created .xml file. And rename the rule to reflect the real file name and not the temporary file name along with a policy name if that was not selected.
I hope this is useful and will save some time when running into issues with unsigned dll’s which we all run into when using Intune and Application Control for Business.